BYOA (Bring Your Own Account)¶
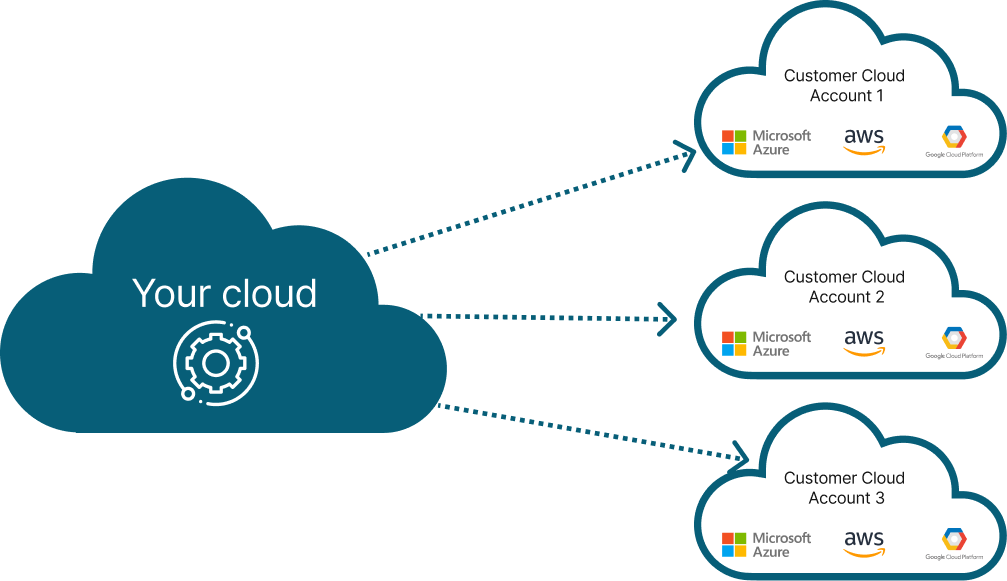
There are many applications that needs to be deployed in customers account due to security and cost reasons. Your customers may prefer to not move the data in your account and want you to deploy your app(s) in their account.
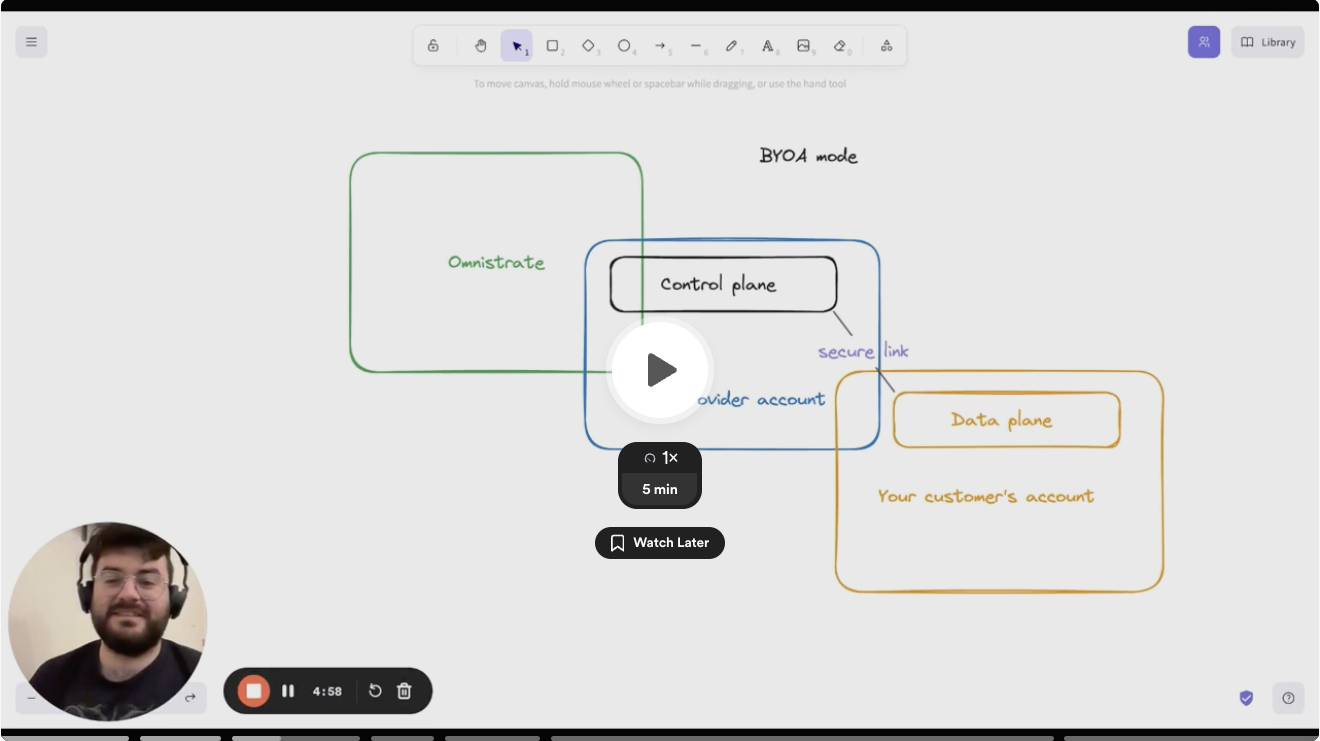
From your perspective, you will have to manage hundreds or thousands of these accounts. This is how the setup may look like:
The challenge is that deploying in your customers account requires manual coordination, sharing of credentials and a lot of operational pain. We have automated the entire process and made it simple to operate in a secure way.
Note
There are several variants of BYOA mode in the industry and they are all somewhat related.
- Bring Your Own Account (BYOA) - in this mode, your customers' brings their account but SaaS provider manages the infrastructure
- Bring Your Own VPC - in this mode, your customer brings a specific VPC to deploy and manage your application
- Bring Your Own Cloud (BYOC) - same as above, where your customers' bring their account but maintains full ownership of the infrastructure. See here for more details
We support different variants of BYOA for you to NOT worry about the complexity of the underlying infrastructure
How to enable BYOA¶
Compose spec¶
If you are using compose spec, you can add the following to your compose to configure your provider account:
x-omnistrate-byoa:
awsAccountId: 'xxxxxxxxxxx' # random account number
awsBootstrapRoleAccountArn: 'arn:aws:iam::xxxxxxxxxxx:role/omnistrate-bootstrap-role'
gcpProjectId: 'xxxxxxxxxxx'
gcpProjectNumber: 'xxxxxxxxxxx3'
gcpServiceAccountEmail: '[email protected]'
azureSubscriptionId: 'xxxxxxxx-xxxx-xxx-xxxx-xxxxxxxxxx'
azureTenantId: 'xxxxxxxx-xxxx-xxx-xxxx-xxxxxxxxxx'
Note
Please don't forget to replace the account numbers, project id and other information with your own account information
APIs¶
If you are using APIs, please refer to this page
Videos¶
- To configure your customer's account using Terraform, you need to follow this video guide
- To configure your customer's account using Cloud Formation, you need to follow this video guide
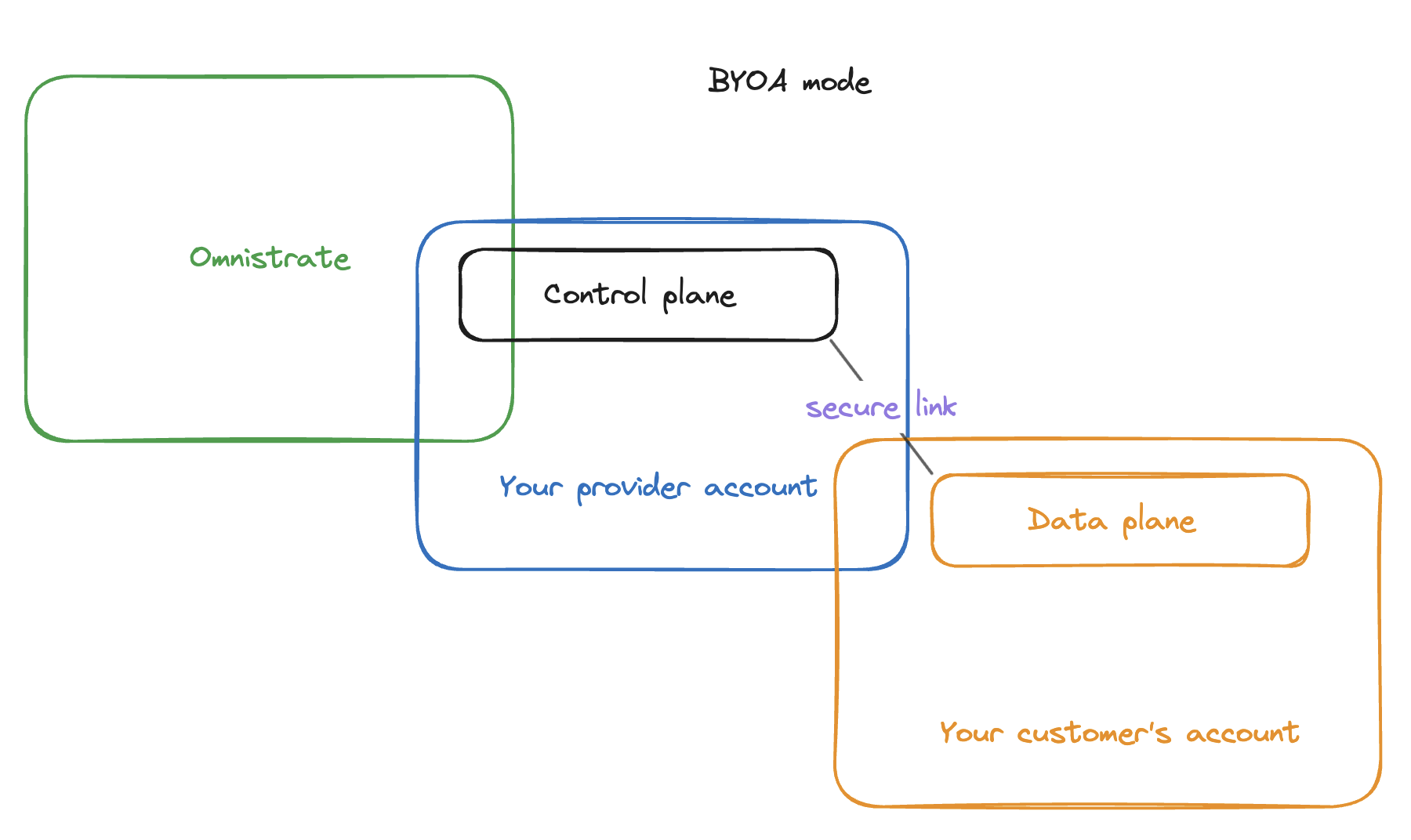
BYOA architecture¶
As discussed here, we build a trust relationship between your account and your customers account to allow you to automate the setup. Once setup, system uses the industry standard secure techniques to reverse the connection to prevent any inbound connections to your customers' account (except while configuring their account during setup), encrypted channel through TLS and oauth tokens to secure the connectivity between your customers account and your account.
If your customers wants to also disable any outbound data, they can also achieve that by updating the IAM permission set. Please reach out to support@omnistrate.com for any questions on this front.
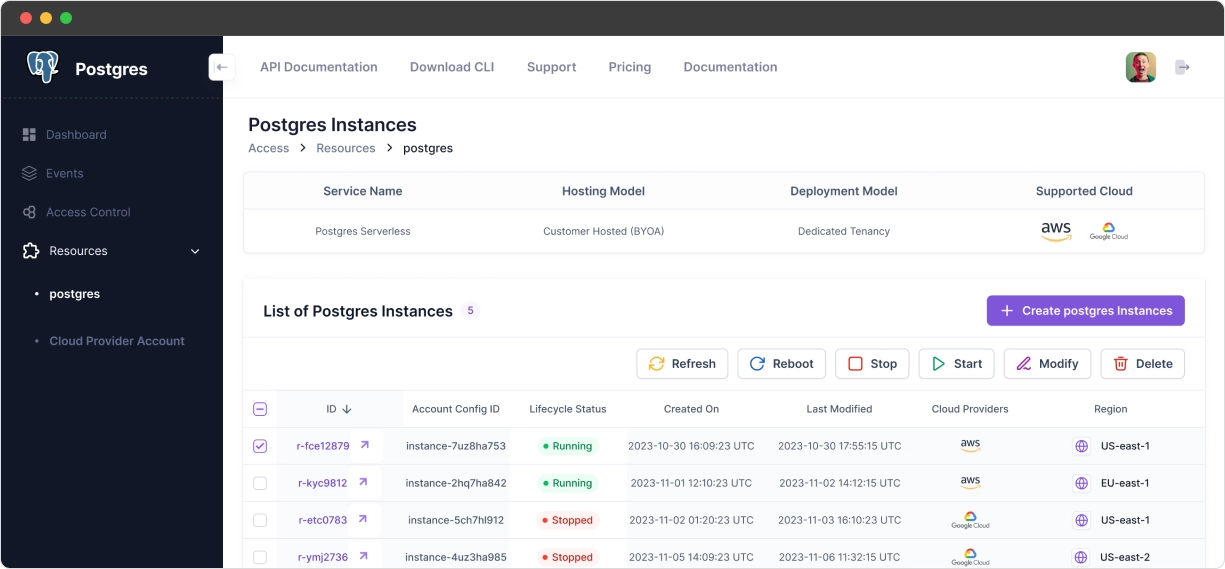
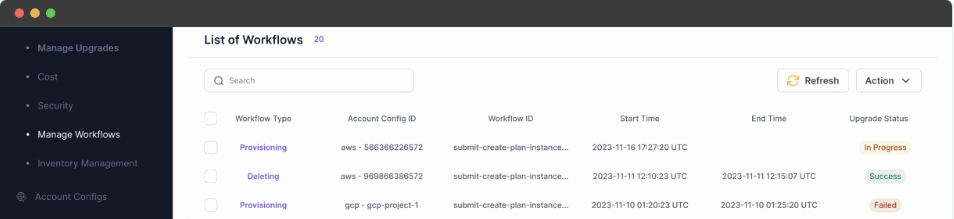
BYOA in action¶
Omnistrate makes it easy to manage resource instances across the fleet
View for your customers¶
Internal view for your teams¶
Demo video¶
Here is a demo video on PostgreSQL BYOA DBaaS:
Bring Your Own VPC (BYO-VPC)¶
If you are running your SaaS in BYOA mode, your customers can bring their own VPC and Omnistrate will deploy your Dataplane in their VPC.
Prerequisites¶
To use BYO-VPC, your customer has to first create the VPC and subnets with the following requirements:
- The VPC needs to enable DNS hostnames and DNS resolution, please refer to this page
- Public NAT gateway is required in the VPC to pull Container Image from repository, also make sure all private subnets route tables have an entry to this NAT gateway, please refer to this page
- The public subnet needs to have auto-assign public IPv4 address enabled, please refer to this page
- All private subnets need to have tag
kubernetes.io/role/internal-elbwith value1and public subnets need to have tagkubernetes.io/role/elbwith value1, please refer to this page
How to get started¶
When creating an instance, your customer can specify VPC id as value of cloud_provider_native_network_id input parameter, and rest of things will be same as regular BYOA experience.